Full Cybersecurity IT Audit / Review
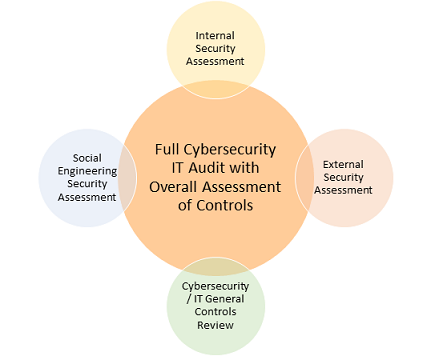
Our full IT audit / review is one of the best and most thorough in the industry. We pride ourselves on being both thorough and practical addressing cybersecurity and IT related risks as well as areas of IT regulatory concern. The scope of the full review includes all of the below assessments and audits.
- Cybersecurity / IT General Controls Review
- Internal Security Assessment
- External Security Assessment
- Social Engineering Security Assessment
We will provide an assessment (satisfactory, needs improvement, or unsatisfactory) for each of the below areas:
- Internal security assessment
- External security assessment
- Cybersecurity / IT general controls review
All respective areas of the Social Engineering Security Assessment will receive a pass or fail based on individual tests/targets/locations.
Contact Us For More Information and Pricing
Or contact us directly at 515-229-5674
Internal Security Assessment
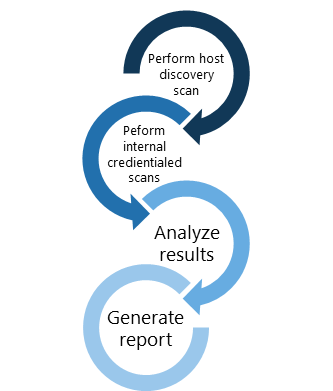
Secure Guard Consulting's internal security assessment involves scanning network assets internally from behind the corporate perimeter firewall, providing a comprehensive view of the organization's IT environment. We scan a defined list of IP addresses that correspond to servers, file sharing systems, printers, employee PCs, etc. to identify any vulnerabilities based on current threats.
The scope of the Internal Network Security Assessment is to determine if internal network security controls are effective in preventing or detecting unauthorized persons from gaining access to data or system functions. Our internal assessment is conducted onsite with an underlying focus on identifying real vulnerabilities and reducing false positives. When possible, Secure Guard Consulting will employ an authenticated (credentialed) scan where an active logged-on session to the operating system will be created allowing the testing process to comprehensively identify risks.
We will provide an assessment (satisfactory, needs improvement, or unsatisfactory) based on the results of the internal security assessment:
Contact Us For More Information and Pricing
Or contact us directly at 515-229-5674
Internal Penetration Testing (Enhanced Testing Option)
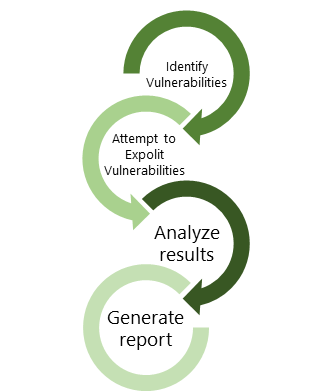
Secure Guard Consulting's Internal Penetration Test is designed to demonstrate what a potential attacker could do if they breached your perimeter defense(s) and were on your internal network. This type of testing mimics the actions of an actual attacker exploiting weaknesses in internal network security without the usual dangers.
The Internal Penetration Test involves going beyond traditional credentialed vulnerability scanning and attempting to exploit identified vulnerabilities.
The scope of the Internal Penetration Test will be to utilize information obtained from the above Credentialed Internal Vulnerability Scanning performed and actively exploit identified vulnerabilities as well as perform other internal penetration tests (e.g., privilege escalation attacks, arbitrary code execution, lateral movement on the network, etc.).
No opinion will be delivered regarding the Internal Penetration Test; we will only provide fact-based data or outcomes of the internal penetration test within the report.
Contact Us For More Information and Pricing
Or contact us directly at 515-229-5674
External Security Assessment / External Penetration Testing
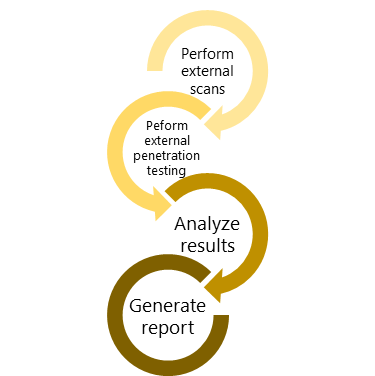
Secure Guard Consulting's external security assessment specifically examines an organization's security profile from the perspective of an outsider or external hacker who is targeting the organization from the internet without access to systems and networks behind the external security perimeter. We provide a variety of options including annual or quarterly external scans.
The scope of the External Security Assessment is to determine if internet security controls are effective in preventing or detecting unauthorized persons from gaining access to data or system functions. Our external assessment is conducted offsite on a defined list of external internet facing IP addresses to identify vulnerabilities while reducing false positives.
NOTE: We provide a variety of options including annual, quarterly, and monthly external scans.
We will provide an assessment (satisfactory, needs improvement, or unsatisfactory) based on the results of the external security assessment:
Contact Us For More Information and Pricing
Or contact us directly at 515-229-5674
Internal and/or External Application Penetration Testing (Enhanced Testing Option)
Whether we're talking about internal applications, internal web based applications, external web facing applications, our application penetration testing has you covered.
The scope of application penetration test will vary depending on the application being tested. Based on the application’s attack surface, generally speaking, we will attempt to brute force into the application, perform SQL injection attacks, directory traversal, etc.
No opinion will be delivered regarding; we will only provide fact-based data or outcomes of the application penetration test within the report.
Contact Us For More Information and Pricing
Or contact us directly at 515-229-5674
Cybersecurity / IT General Controls Review
The scope of the Cybersecurity / IT General Controls Review (including GLBA compliance) included a review of the information systems in use by your organization, and a review of the technical, administrative, and physical safeguards associated with maintaining the security and confidentiality of customer information. The review will include an in-depth review of documentation related to your organization’s information security program. In addition, interviews will be held with key members of the staff.
Some of the areas that will be covered during the Cybersecurity / IT General Controls Audit/Review include the following:
- Information Security Program
- IT Risk Assessment
- Document security
- Change management
- Audit program
- Operations
- Network remote access
- System logging and monitoring
- Separation of duties
- IT management
- Internet banking (including CATO)
- Web site
- Systems authentication
- Network services
- Electronic funds transfer (EFT)
- Incident response
- Core banking system
- Security awareness training
- IS/IT policies and procedures
- Wire transfer
- Imaging
- Automated Clearing House (ACH)
- Customer identification procedures
- Backup procedures
- Branch/Remote capture
- Information Security Strategy
- Access Controls
- Authentication
- Network Access
- Application Access
- Remote Access
- Physical and Environmental Safeguards
- Encryption
- Patch Management
- Malicious Code Prevention
- Configuration and Change Control
- Personnel Security
- Data Security
- Service Provider Oversight / Vendor Management
- Business Continuity / Disaster Recovery
- Insurance
- Security Monitoring / Firewall Administration
- GLBA Compliance
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
The Cybersecurity / IT General Controls review will involve 2-5 days onsite with remaining conversations occurring via phone and email.
We will provide an assessment (satisfactory, needs improvement, or unsatisfactory) based on the results of the Cybersecurity / IT general controls review
Contact Us For More Information and Pricing
Or contact us directly at 515-229-5674
Social Engineering Security Assessment
Our Social Engineering Assessment is based on current “real world” scenarios. All assessments are accomplished in a way that there is no actual infringement or damage on your network, computers, or users and include no permanent installation of damaging programs and no affect to the user’s computer or environment.
The scope of services for this social engineering assessment may cover one or more of the following threat vectors (as per agreement):
- Email - A uniquely crafted email is sent to a set of users that attempts to gather information by having them click on a link to a “fake” web page (such as a fake Outlook Web Access page) and request data such as password information. No malicious program shall actually be installed. CIO will be notified of all information gathered in order to remediate in a timely manner.
- * Email assessment target range is a sampling of employees.
- Phone - A social engineering attack is executed against an agreed upon set of limited users via a phone attack, utilizing phone spoofing and social engineering methods.
-
* Target range size is agreed upon prior to assessment services.
- In-person - A social engineering attack is executed against an agreed upon locations where the assessment will be in person. For example, unescorted attempt to enter authorized areas (What is the reaction of employees and security personnel?)
-
* Target range size is agreed upon prior to assessment services.
No opinion will be delivered; we will only provide fact-based data or outcomes of the social engineering security assessment within the report.
Contact Us For More Information and Pricing
Or contact us directly at 515-229-5674
Active Directory (AD) Password Cracking Audit
Our AD password audit will involve extracting cryptographic hashes of passwords from the bank’s Active Directory. With those hashes, we will then attempt to 'crack' or decrypt these hashes to reveal the actual plaintext passwords. The goal is to assess the strength of user passwords across the organization and identify potential vulnerabilities arising from weak password practices.
Process:
- Extraction of Hashes: Using PowerShell run from a laptop shipped onsite (ideally onsite for internal security assessment work performed already), password hashes will be extracted from the AD database. These hashes represent encrypted forms of the actual user passwords and serve as a basis for the audit.
- Password Cracking: Utilizing powerful password-cracking tools and techniques like dictionary attacks, brute-force attacks, and rainbow tables, as well as application of various rulesets, the extracted hashes are subjected to decryption attempts. The objective is to uncover as many plaintext passwords as possible from their hashed forms.
- Analysis: After cracking the hashes, the results are analyzed. Weak or easily cracked passwords are identified, and patterns in password creation are observed.
- Report: A comprehensive report detailing the findings is produced. This includes the number of weak passwords, common patterns observed, and recommendations for strengthening password policies. A couple of options are available.
- We provide only the passwords obtained with a list of the respective usernames, but we do not link the two together. This way, if someone’s password was cracked (and by definition, weak), IT can force a password reset on that individual and provide training to that individual.
- We provide the passwords obtained and link them to their respective usernames. Similar to the above, password resets and training could be done, but this has an added benefit of being able to take that password that was cracked and try to log into various other bank applications (internal and web based) to see if that password is being reused. This would be performed by the bank and not SGC.
• This option is probably the best option if your bank has MFA implemented for all employee network logins, as you’re able to then test whether password reuse is occurring across various other applications.
- We provide only the passwords that were cracked with no usernames. While training individual users whose passwords were deemed weak is important, some banks will globally train all personnel. By showing the passwords that were cracked to everyone, those individuals should see them and reset their passwords.
No opinion will be delivered; we will only provide fact-based data or outcomes of the social engineering security assessment within the report.
Contact Us For More Information and Pricing
Or contact us directly at 515-229-5674
PLEASE COMPLETE THE BELOW INFORMATION AND WE WILL REACH OUT TO YOU SOON!
